Wine in one of the them. Many Linux OS have already started providing wine by default like linux Mint, Kubuntu etc.
Wine is a compatibility layer for running Windows programs. It is a completely free alternative implementation of the Windows API consisting of 100% non-Microsoft code.
Before you get started, you may want to check and confirm that the Windows program you want to install is in fact supported by Wine. Visit the Wine Application Database for a list of all the programs known to work in Wine, and at what level (fully supported, needs some tweaking, etc).
There is another software called Crossover
which requires registration. Visit this site http://www.howtogeek.com/howto/linux/how-to-install-windows-applications-on-linux-using-crossover/ for further information
If you don't want any hassle of installing packages in linux like Wine & Crossover, I suggest these alternatives.
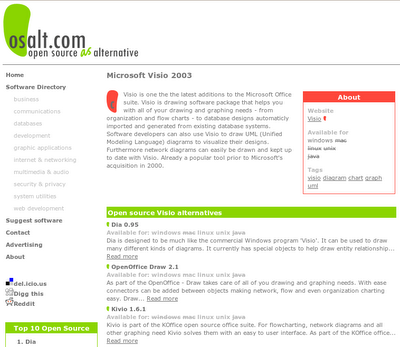
1> Search for open source alternatives. There are plenty of alternatives available in market like gimp instead of Photoshop, openoffice instead of Microsoft office, BriscCad instead of Autocad.
I feel like, you are not satisfied yet. Goto www.osalt.com.
On that site, you can enter the name of the Windows application and it will list the open source alternatives that provide similar functionality.
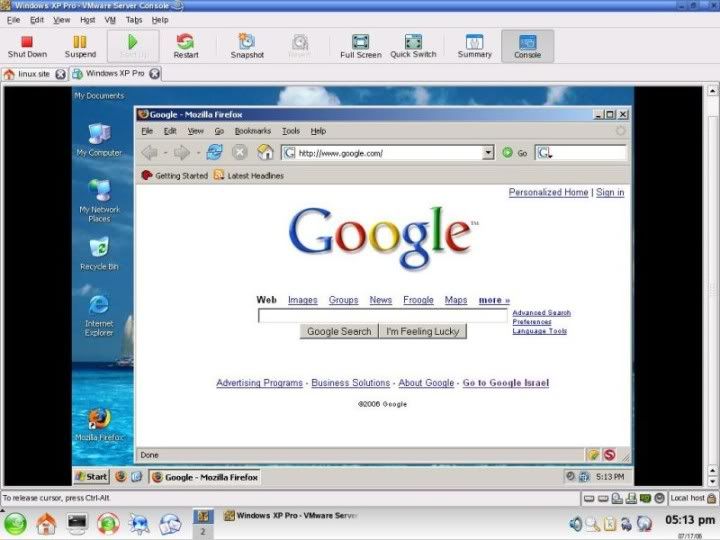 2> Run windows in a virtual machines. Some of the solutions available are VmWare & VirtualBox. Install windows inside linux & work in it.
2> Run windows in a virtual machines. Some of the solutions available are VmWare & VirtualBox. Install windows inside linux & work in it. 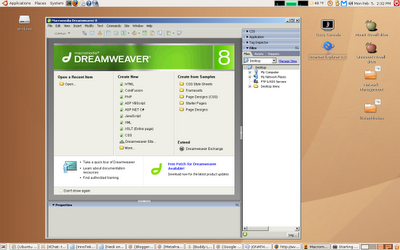 |
| Citrix |
If you want it other way round i.e. running linux software in windows,
check this out -->http://hacks-tweaks-security.blogspot.com/2010/04/creating-linux-environment-installing.html



